Go Eco-friendly: Effective and Secure Computer Recycling Options
Go Eco-friendly: Effective and Secure Computer Recycling Options
Blog Article
Secure Data Damage and Computer Recycling Services for Organizations
In an age where data violations and personal privacy concerns are coming to be significantly widespread, making certain the protected damage of delicate info has actually ended up being a crucial duty for organizations. This is where specialist safe and secure information damage and computer recycling services come right into play. Just how precisely does protected information destruction work?
Importance of Secure Data Devastation
Safe and secure information damage is of utmost significance for services to secure sensitive details and avoid potential information breaches. In today's electronic age, where data is an useful possession, companies have to take proactive steps to ensure that their personal information is safely destroyed when it is no much longer needed. Failing to do so can subject companies to substantial dangers, consisting of monetary loss, reputational damage, and legal implications.
When sensitive information is not properly ruined, it can fall under the incorrect hands, leading to data breaches and identity theft. Cybercriminals are frequently looking for opportunities to make use of weak security procedures and obtain unapproved access to beneficial info. By applying safe information destruction techniques, companies can minimize these risks and protect their delicate data.
Protected data devastation involves the irreversible and complete damage of all data stored on electronic gadgets, such as disk drives, solid-state drives, and smart phones. This procedure makes sure that the data can not be recovered or accessed by unauthorized individuals. It is important to make use of reliable data destruction methods, such as degaussing, shredding, or data wiping using specialized software application, to make sure the full elimination of information.
Furthermore, safe information devastation is not just vital for shielding sensitive customer information but also for regulatory compliance. Many markets, such as medical care and financing, have stringent data protection policies that need organizations to safely take care of sensitive information (computer recycling). Failure to abide with these regulations can result in extreme penalties and legal repercussions
Benefits of Specialist Computer Recycling
As companies prioritize secure information devastation, they can likewise reap the benefits of specialist computer recycling services. Specialist computer reusing offers many benefits for organizations aiming to take care of their old or outdated devices in a environmentally friendly and responsible manner.
Among the main benefits of expert computer system recycling is the assurance that delicate information is totally and firmly removed from all gadgets. This eliminates the danger of information breaches and makes sure conformity with data defense regulations. By utilizing specialist solutions, companies can have satisfaction understanding that their information is being dealt with and ruined appropriately.
Along with data safety, expert computer recycling likewise assists services reduce their influence on the atmosphere. Electronic waste, or e-waste, contains dangerous compounds such as mercury, lead, and cadmium, which can leach into the dirt and water otherwise disposed of properly. Specialist recyclers have the understanding and knowledge to securely get rid of and remove of these dangerous materials, decreasing the ecological impact of digital waste.
Moreover, professional computer recycling promotes sustainability by helping with the reuse and healing of beneficial resources. Recycling old computers and IT devices enables the removal of valuable metals and elements, which can then be made use of in the manufacturing of new tools - computer recycling. This lowers the requirement for raw materials and power intake, contributing to a much more round and lasting economy
Actions to Ensure Information Safety Throughout Destruction
To ensure miraculous data safety during the destruction procedure, services have to follow a series of meticulous steps. These actions are necessary to stop any kind of potential information violations and protect sensitive information from falling right into the wrong hands. The initial action is to examine the data that requires to be damaged. This includes identifying all the storage space tools and making sure that no information is forgotten. When the inventory is total, the following action is to select the proper technique of devastation. Options include physical destruction, such as shredding or squashing, or degaussing and overwriting for magnetic media. The picked method must be certified with industry standards and guidelines.
After choosing the devastation method, it is essential to entrust the task to a licensed and trustworthy data damage provider. These companies have the competence and customized tools to find more perform the devastation process securely. It is important to develop a chain of protection and obtain a certification of damage as evidence that the information has been damaged appropriately.
Furthermore, companies need to also think about executing data encryption and safe disposal methods within their organization. Encrypting sensitive data ensures that even if it comes under the wrong hands, it continues to be unreadable and unusable. Protected disposal techniques involve securely getting rid of data from storage tools before deactivating or repurposing them.
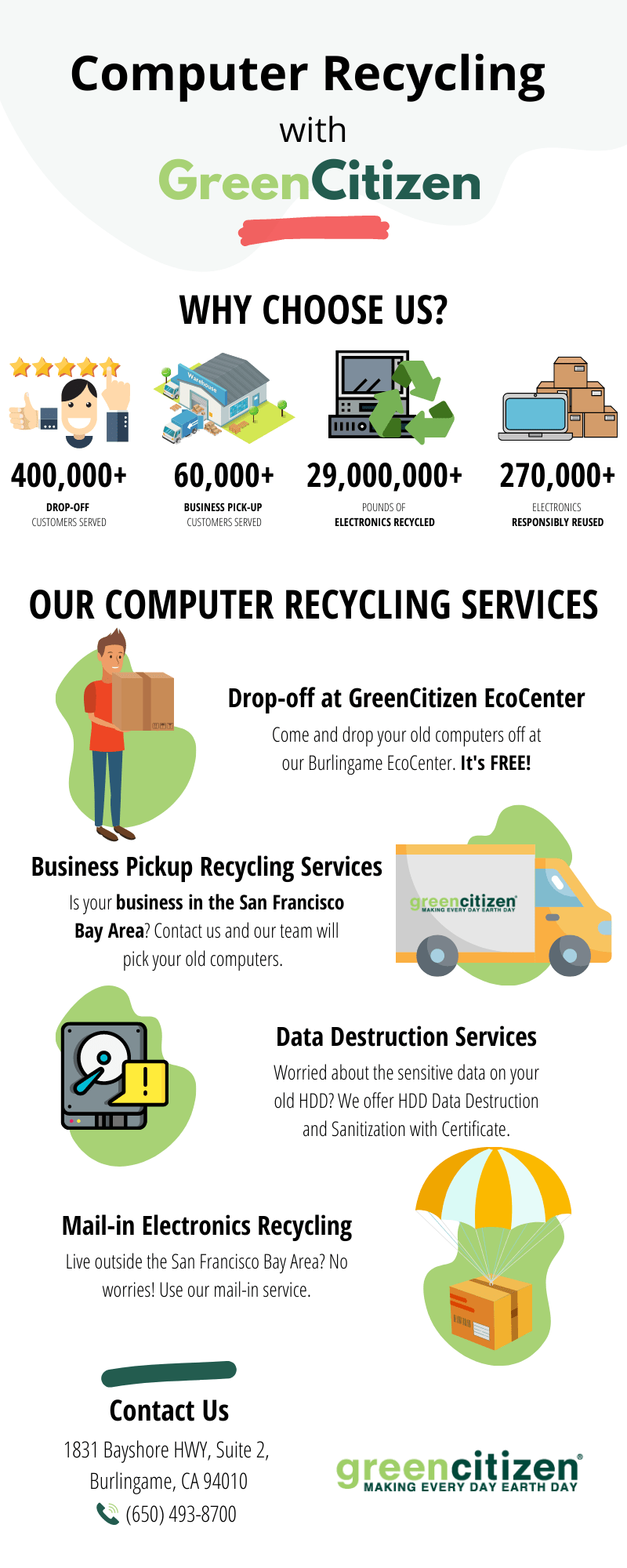
Eco-Friendly Techniques for Computer System Disposal
In accordance with liable information devastation and computer recycling techniques, services should likewise focus on the usage of environmentally friendly approaches when dealing with their computer systems. With the increasing issue for environmental sustainability, it is essential that businesses take on measures that decrease the impact of computer system disposal on the atmosphere. Among one of the most efficient ways to achieve this is via correct reusing procedures.
When it pertains to environment-friendly computer disposal, recycling is the key. Reusing permits the healing and reuse of important products, reducing the need for source removal and decreasing waste. By reusing computers, businesses can aid preserve all-natural resources, lower greenhouse gas discharges, and prevent poisonous materials from entering the setting.
To guarantee eco-friendly computer system disposal, services ought to companion with certified recycling firms that stick to strict ecological standards. These business have the expertise and framework to safely take down and recycle computers, removing useful parts such as metals, plastics, and glass for reuse. They additionally make sure that harmful materials, such as lead, mercury, and brominated flame resistants, are correctly handled and disposed of in an ecologically liable manner.
Along with reusing, services can additionally consider donating their computer systems to philanthropic organizations or institutions. This not just expands the lifespan of the gadgets yet also offers accessibility to modern technology for those that might not description have the methods to afford it. Nevertheless, it is essential to make certain that the donated computers are in great functioning problem and have been appropriately cleaned of any sensitive data.

Selecting the Right Secure Information Destruction Provider
When picking a safe data destruction service provider, organizations must prioritize companies that have a tested record of carrying out robust information defense measures. It is important for companies to make sure that their delicate details is taken care of and damaged safely to avoid any potential data breaches or unauthorized gain access to. Selecting the ideal information destruction provider is of utmost importance.
When choosing a supplier is their accreditation and compliance with sector criteria,One crucial aspect to think about. Search for service providers that adhere to extensively identified requirements such as ISO 27001, which guarantees the execution of efficient information safety and security management systems. In addition, accreditations like NAID AAA (National Organization for Information Destruction) give guarantee that the company follows finest methods in data devastation.

In addition, companies ought to analyze the copyright's data dealing with procedures, consisting of the chain of custody and transportation processes. Make sure that the company follows stringent methods for gathering, delivering, and saving the information securely throughout the damage procedure.
Finally, think about the copyright's track record and customer testimonials. Research study the company's history, checked out reviews, and request recommendations from previous clients. This will assist determine the company's degree of dependability, professionalism and trust, and consumer fulfillment.
Conclusion
To conclude, secure data destruction and professional computer system reusing solutions are necessary for companies to safeguard delicate info and comply with ecological guidelines. By complying with correct steps to guarantee information security during destruction and utilizing environment-friendly disposal approaches, services can secure their data and contribute to a lasting future. It is crucial for businesses to pick the appropriate safe data devastation copyright to make certain the greatest level of security and compliance.
Secure information damage is of utmost significance for companies to protect sensitive details and stop potential information breaches. By applying safe and Full Report secure data destruction methods, companies can minimize these threats and guard their sensitive information.
Protected information devastation includes the complete and permanent destruction of all information kept on electronic gadgets, such as tough drives, solid-state drives, and mobile tools. It is critical to utilize dependable information destruction techniques, such as degaussing, shredding, or information wiping utilizing specialized software, to make sure the complete elimination of data.
When picking a safe and secure information destruction copyright, businesses should focus on companies that have a tested track document of implementing robust information protection measures.
Report this page